Splunk on honeypots
 |
| "Sheilds Up!" |
I last wrote about honeypots back in October last year when I published the results of a WordPress honeypot that I'd been running for almost 100 days. That was my first and since then I've always had a handful on the go. I don't usually use any sort of honeypot distro, rather I prefer to 'bake my own' or in some cases re-purpose or replace some and services within a network to make a sort of patchwork, distributed honeypot.
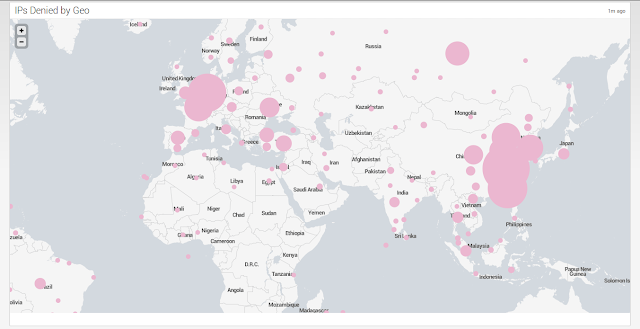
One practice which seems to have become almost a habit now is to install Splunk somewhere and use that to correlate (in the loosest sense of the term) the events observed. In the absence of a SIEM (an lets face it, a lot of companies just aren't there yet) it's a great way to convert those logs into intelligence and provide reporting as well as providing a user friendly interface for analysts and consumers to explore the data with.




