Splunk Security Cheat Sheet

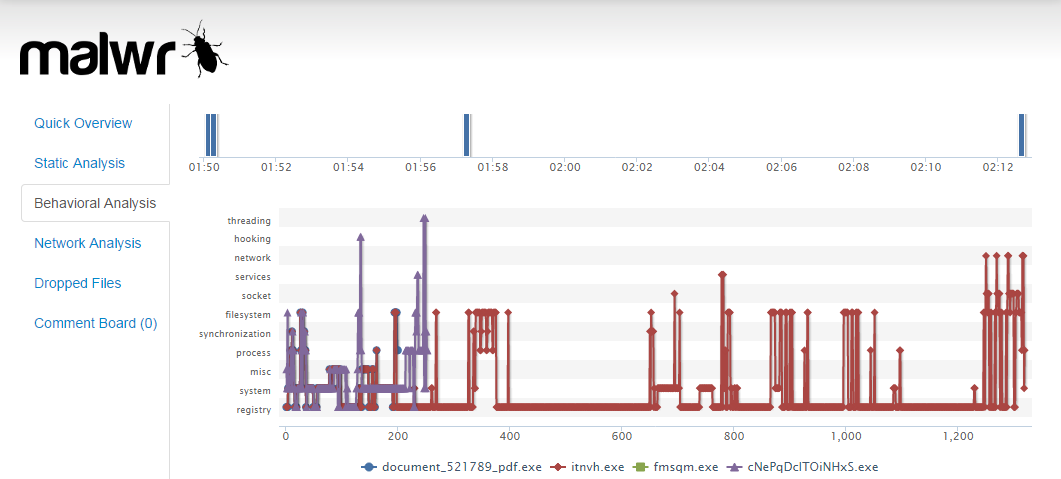
Apart from being a source of all too frequent and embarrassing typos, Splunk is a big data platform which allows you to interrogate data and present results is a variety of contexts and visualisations. I've been using it for a little over 12 months, self teaching or Googleing as I go, predominantly to sift through the terabytes of logs from various applications and appliances that get generated in my 9-5 every day. You can use Splunk to build dashboards which are typically better than the ones that come with the product ( full size ) I've started to pull together all the searches, notes and bits of code into a sort of security cheat sheet which I thought would be a good thing to share as well as providing some real world examples of how you might use Splunk in a security context. Cheat Sheet I'm actively working back through my notes and adding to this all the time so it might be a good thing to reference via the URL or re-visit from time to time. I'll t...