Online malware sandboxes - a real world blind taste test
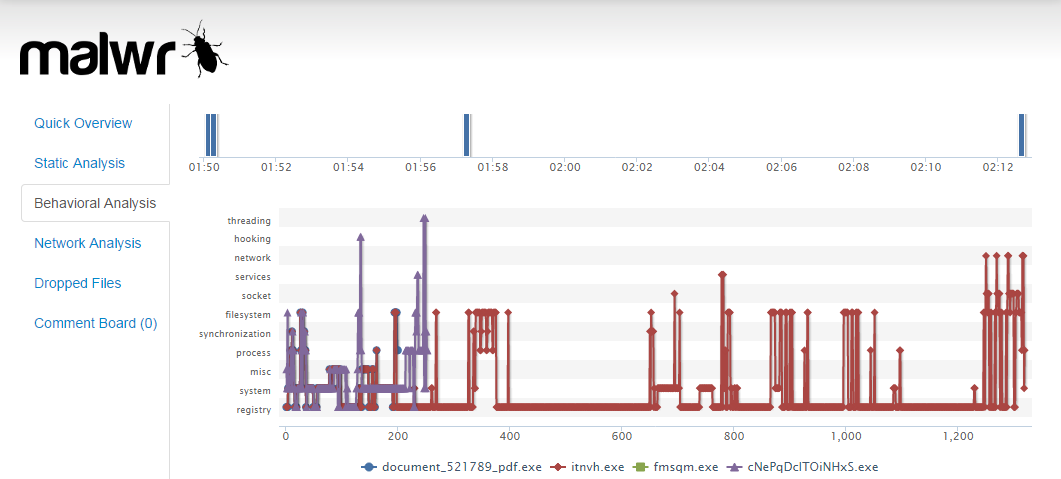
I don't think I'd had chance to get my seat warm on Monday when I was approached by our service support function who were getting inundated with details about a 'virus' doing the rounds at via email which, when opened, forwarded itself to everyone in the user's address book. I don't normally get involved with desktop issues but I'm always happy to help and eager to understand risks both technically and from a wider business perspective. It seemed our endpoint anti-virus 'solution' had a 0% first-time detection success rate and by this time it had already managed to sneak past our 3rd party email security gateway. I set about acquiring a copy of the offending payload and decided that it would make a good candidate for a 'blind taste test' to run past a few online sandboxes. If you're not familiar with the concept, sandboxes are controlled environments within which you can run un-trusted programs and capture details about how they behave.