Wordpress Honeypot - Part 1
Honeypots are currently in vogue with lots of security researchers writing about how they can be used to profile adversaries and detect emerging threats.
Once configured I performed the kind of DNS enumeration you might expect an attacker to perform during reconnaissance in order to ensure the records were returned and appeared legitimate using Fierce:
Despite my efforts to make the site look as legitimate as possible, I couldn't help myself and threw in a couple of 'easter eggs' which I hoped a semi-observant attacker might pick up on:
I ran a Wordpress honeypot last year for little more than three months as a little exercise in setting up, running and then monitoring the results produced by these invaluable security tools. I decided that as a first attempt, I'd use it to attempt to assess the average level of technical capability of those individuals or parties that seek to identify and exploit common web applications. Anyone who reviews the logs of any website, big or small, can tell you that these kinds of attack form a huge percentage of the 'background' noise of the internet. I never really intended to share the details or results of this exercise but I've since changed my mind and hope that if you too have considered setting up and running your own that my 'notes' might encourage you to do so.
As soon as I started playing around with the idea of setting up a honeypot I decided that it should look as real as possible to the attackers, so I signed up for VPS with one of the big names, installed Arley MvBlain's 'Faux WP-Admin' honey pot and then went looking for a domain name. After giving it some consideration I decided to make it look like a website belonging to a regular business and that this business should be something non-technical, the kind of business that will always be bricks and mortar. In the end I decided a garage would be a good identity to assume, but I didn't want to attract false positives by picking a name that would potentially be likened to an actual garage or one so generic that it might easily be stumbled upon. In the end, I did a quick internet search for fictional towns and settled on Capeside (the fictitious setting for Dawson's Creek). I then registered CapesideAutos.com, along with my registrars domain privacy offering.
As soon as I started playing around with the idea of setting up a honeypot I decided that it should look as real as possible to the attackers, so I signed up for VPS with one of the big names, installed Arley MvBlain's 'Faux WP-Admin' honey pot and then went looking for a domain name. After giving it some consideration I decided to make it look like a website belonging to a regular business and that this business should be something non-technical, the kind of business that will always be bricks and mortar. In the end I decided a garage would be a good identity to assume, but I didn't want to attract false positives by picking a name that would potentially be likened to an actual garage or one so generic that it might easily be stumbled upon. In the end, I did a quick internet search for fictional towns and settled on Capeside (the fictitious setting for Dawson's Creek). I then registered CapesideAutos.com, along with my registrars domain privacy offering.
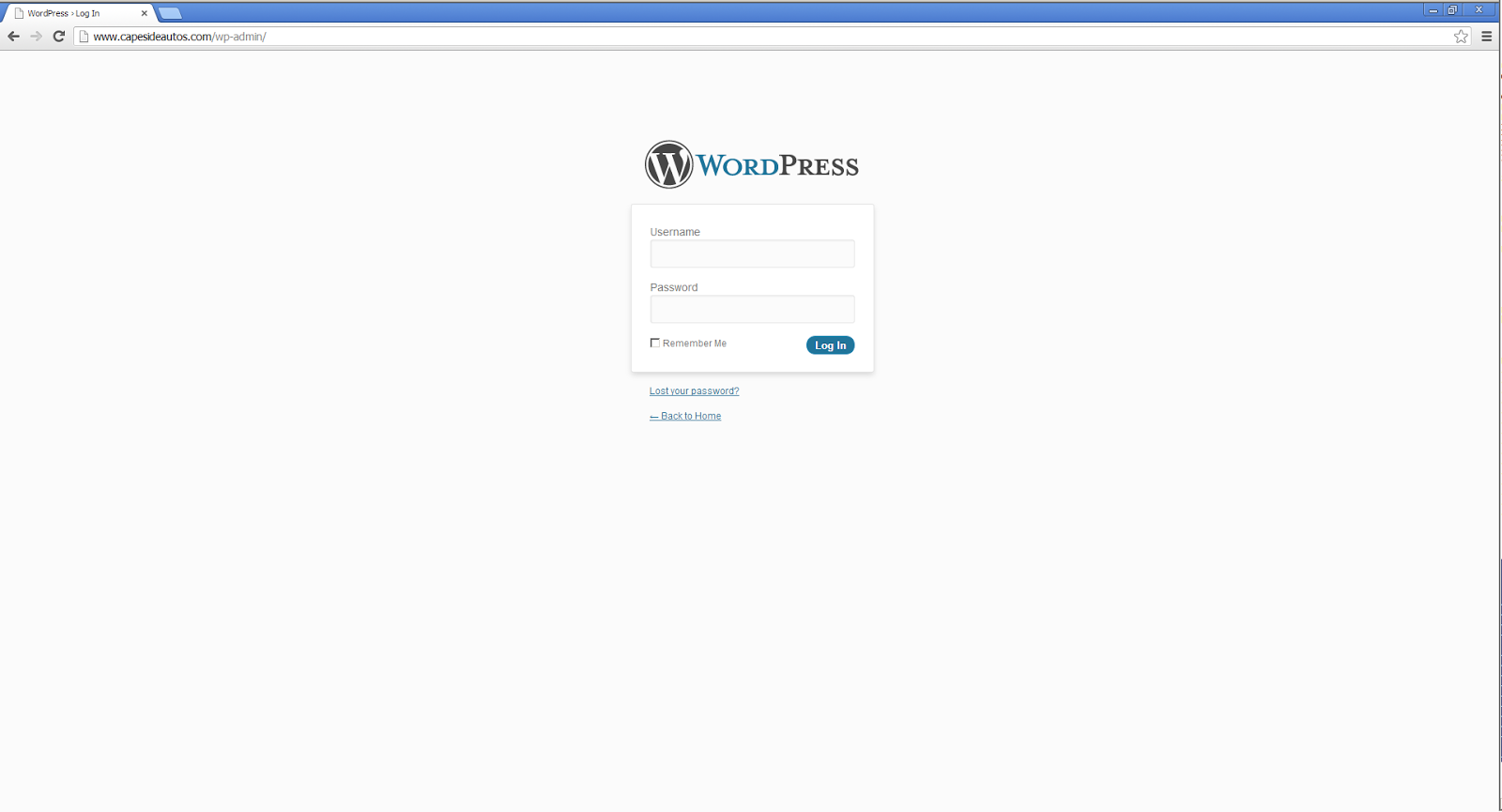 |
| Faux WP-Admin installed |
With the domain registered and architecture in place I set up the kind of typical DNS entries that you might see for any small business:
- CapeSideAutos.com
- Blog.CapesideAutos.com
- LocalHost.CapesideAutos.com
- Mail.CapeSideAutos.com
- www.CapesideAutos.com
Once configured I performed the kind of DNS enumeration you might expect an attacker to perform during reconnaissance in order to ensure the records were returned and appeared legitimate using Fierce:
# ./fierce.pl -dns capesideautos.com
DNS Servers for capesideautos.com:
ns1.sitelutions.com
ns4.sitelutions.com
ns2.sitelutions.com
ns5.sitelutions.com
ns3.sitelutions.com
Trying zone transfer first...
Testing ns1.sitelutions.com
Request timed out or transfer not allowed.
Testing ns4.sitelutions.com
Request timed out or transfer not allowed.
Testing ns2.sitelutions.com
Request timed out or transfer not allowed.
Testing ns5.sitelutions.com
Request timed out or transfer not allowed.
Testing ns3.sitelutions.com
Request timed out or transfer not allowed.
Unsuccessful in zone transfer (it was worth a shot)
Okay, trying the good old fashioned way... brute force
Checking for wildcard DNS...
Nope. Good.
Now performing 2280 test(s)...
176.58.116.166 blog.capesideautos.com
127.0.0.1 localhost.capesideautos.com
176.58.116.166 mail.capesideautos.com
176.58.116.166 www.capesideautos.com
Subnets found (may want to probe here using nmap or unicornscan):
127.0.0.0-255 : 1 hostnames found.
176.58.116.0-255 : 3 hostnames found.
Done with Fierce scan: http://ha.ckers.org/fierce/
Found 4 entries.
Much like the DNS checks, I wanted to make sure the site as a whole appeared legitimate so I scanned it with nikto, a widely used web app vulnerability scanner to ensure the Wordpress admin login was detected:
# ./nikto.pl -host www.capesideautos.com
- ***** SSL support not available (see docs for SSL install) *****
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 176.58.116.166
+ Target Hostname: www.capesideautos.com
+ Target Port: 80
+ Start Time: 2013-08-09 21:30:02 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache
+ Server leaks inodes via ETags, header found with file /, inode: 149461, size: 410, mtime: 0x4e38a794e28c0
+ The anti-clickjacking X-Frame-Options header is not present.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE
+ Retrieved x-powered-by header: PHP/5.3.3
+ /wp-admin/: Admin login page/section found.
+ 6545 items checked: 0 error(s) and 5 item(s) reported on remote host
+ End Time: 2013-08-09 21:30:13 (GMT0) (11 seconds)
---------------------------------------------------------------------------
‘HiddenLogin’ – A Hex Encoded Set of Credentials:
CapeSideAutos-user-capeside-pass-mag1c1091
%43%61%70%65%53%69%64%65%41%75%74%6F%73%2D%75%73%65%72%2D%63%61%70%65%73%69%64%65%2D%70%61%73%73%2D%6D%61%67%31%63%31%30%39%31
‘Cardpayments’ – A Base64 Encoded backup file (.bak)
/admin/cardpayments/backup/admin/paypal/roger.bak
L2FkbWluL2NhcmRwYXltZW50cy9iYWNrdXAvYWRtaW4vcGF5cGFsL3JvZ2VyLmJhaw==



