I don't think I'd had chance to get my seat warm on Monday when I was approached by our service support function who were getting inundated with details about a 'virus' doing the rounds at via email which, when opened, forwarded itself to everyone in the user's address book. I don't normally get involved with desktop issues but I'm always happy to help and eager to understand risks both technically and from a wider business perspective. It seemed our endpoint anti-virus 'solution' had a 0% first-time detection success rate and by this time it had already managed to sneak past our 3rd party email security gateway. I set about acquiring a copy of the offending payload and decided that it would make a good candidate for a 'blind taste test' to run past a few online sandboxes.
If you're not familiar with the concept, sandboxes are controlled environments within which you can run un-trusted programs and capture details about how they behave. They can be invaluable for security analysts, allowing them to detonate malware and extract details about how the payload behaves, what it changes on the system and what network traffic the payload generates.
I did a quick internet search for 'malware sandbox online' and picked the first three that allowed me to upload a file without having to register or provide any details.
Note: This isn't a detailed comparison or analysis of the technology - this is a real world 'apples-for-apples' comparison of how three online sandboxes handle an identified malicious file.
Malwr.com
I instantly recognised malwr.com from security articles I'd read in the past. It's a hosted instance of the
Cuckoo Sandbox and out of the three online sandboxes I tried, it yielded the best results and I'll happily admit that its now my default, go-to-sandbox.
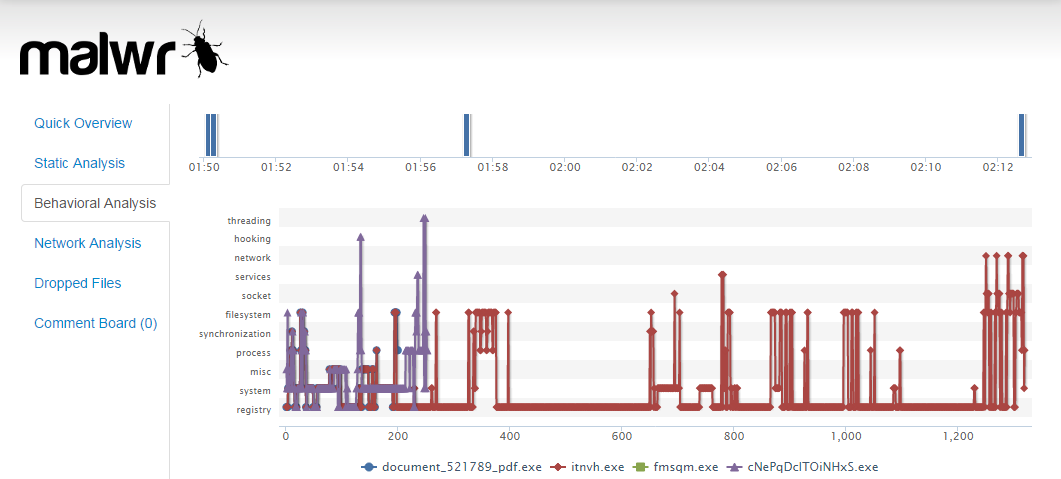 |
| malwr.com - Behavioral analysis |
The break down is full and detailed but intelligently organised as to allow analysts to extract key pieces of information quickly. I was particularly interested in what network traffic the payload generated as this was something I could do something about by denying traffic to identified IP addresses or domains. At the very least, if you can report on network behavior you might stand some chance of identifying all the other clients that might be impacted by reviewing firewall and DNS logs.
 |
| Network analysis - domains |
 |
| DNS traffic for identified domain |
In addition to the break down malwr.com provides, it also hooks into services like virustotal which provide some idea of what your exposure is from a client anti-virus point of view.
Results:
malwr.com
anubis.iseclab.org
 |
| anubis.iseclab.org |
The anubis sandbox came very close to the malwr.com output but the results missed some of the domains. All I can think is that the payload wasn't perhaps allowed to run for long enough which is a shame really because the reporting options and level of detail provided within was excellent.
 |
| anubis.iseclab.org - reporting |
I'll certainly be looking to use the anubis sandbox again and giving it the chance to demonstrate its own merits and strengths.
Results:
anubis.iseclab.org
camas.comodo.com
I'll be honest, I only know Comodo as a CA so was a little surprised to find that they offered a malware sandbox. I held no expectations either way and proceeded to upload the same payload that I'd uploaded to the other two sandboxes and then hit then waited to see how it compared...
 |
| camas.comodo.com |
 |
| Comodo results - .zip |
The site appeared to look like it was working but soon after uploading the file it returned an error. I haven't had chance to go back and look at the cause but suspect that it couldn't handle the zip format. There is no warning about file types supported on the upload page and I didn't really fancy unpacking executables so I just left it there. I'll probably look at it again in the future and I'm sure it too will demonstrate its own merits and strengths.
Results:
camas.comodo.com









